Identity Governance & Administration
Identity Governance & Administration
IGA (Identity Governance & Administration) is a subcategory of IAM (Identity & Access Management). Although it is sometimes incorrectly used as a successor term, the term IGA was coined by Gartner a few years ago and has since been used for the corresponding Magic Quadrant.
Identity Governance & Administration is used to express that the control, traceability, and compliance of digital identities are in the foreground. These things are at the heart of modern IT security, especially when it is oriented around the so-called zero trust model.
An IGA solution manages and secures digital identities for all users, applications, IoT devices and data. It enables organizations to provide automated access to an ever-growing number of technology assets while managing potential security and compliance risks.
What are the benefits of IGA?
Reduces IT operational costs
Reduces risk and increases security
Improves compliance
Faster and more efficient access to the enterprise
Solutions
Architecture consulting and consulting at SKyPRO are independent of the solution used. Technology is an important factor, but only one of several.
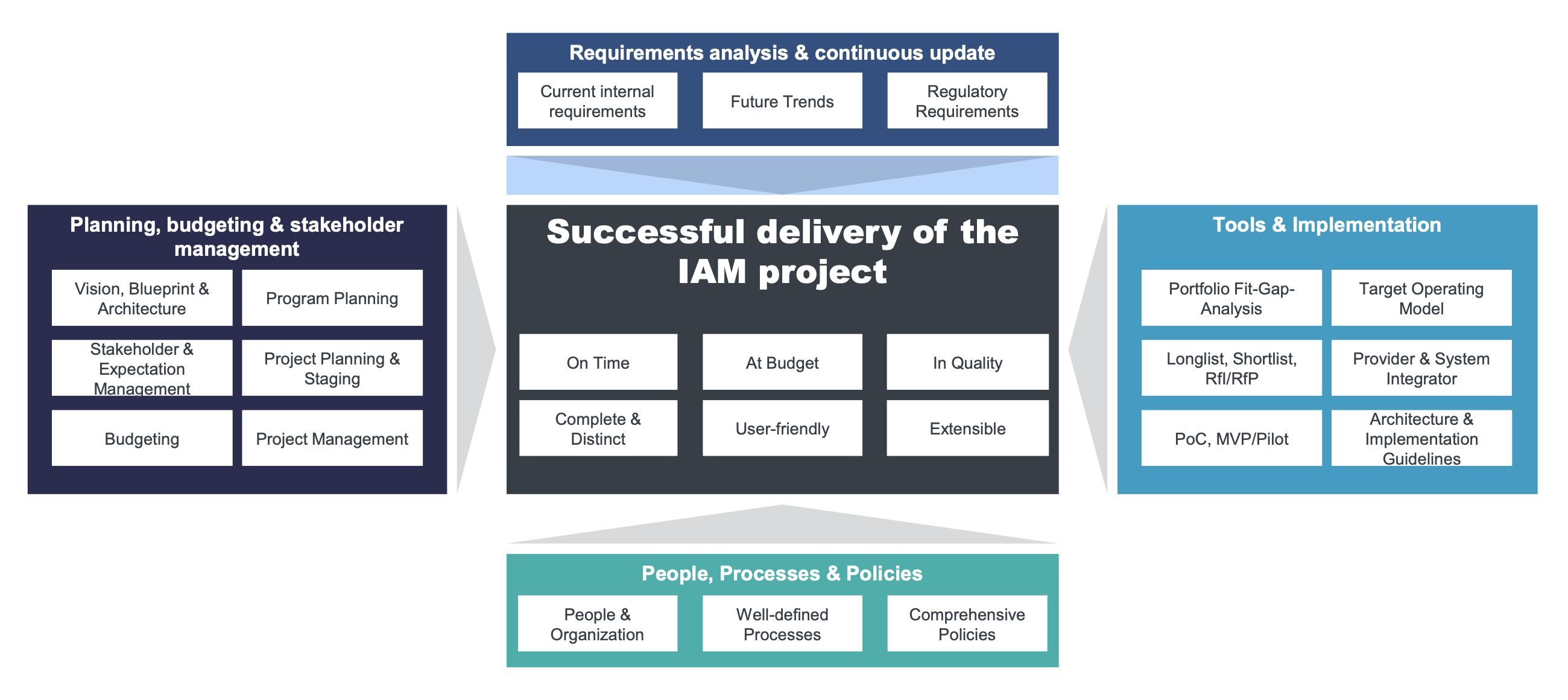
Key Success Factors for IAM Projects: Architecture is Essential for Success in IAM; KuppingerCole, 2022.
From a technological perspective, we also work intensively with the NetIQ solution portfolio from OpenText and have done so since the release of the first version over 20 years ago. This gives us one of the largest pools of expertise in the world, especially in the DACH region. Moreover, we work with renowned partners selected for their top quality and experience. You can rely on this collective expertise.
There are many IGA solutions and meanwhile also many good ones. Here are the reasons why we have decided to keep our focus on NetIQ:
- Stability and reliability (over 20 years on the market)
- Regular leader in the KuppingerCole Leadership Compass
- Completeness (provisioning, workflows, recertification, role mining, risk, advanced authentication, single sign-on, …)
- Real-Time Provisioning
- Scalability (number of objects and number of events per time unit)
- Number of technical interfaces (from RACF to REST and SCIM)
- Flexibility (schema extensions are the order of the day)
- The powerfulness of the workflow engine (functionality)
- Interaction between driver and workflow engine
- Many long-standing, satisfied customers – from small to very large.
The most important solutions from the IGA portfolio:
| Component | Description | More info |
| Identity Manager | Extremely scalable identity management with flexible workflows, real-time event-based provisioning based on what we believe is the world’s best ID Vault (eDirectory) and user self-service portal. | https://www.microfocus.com/en-us/cyberres/identity-access-management/identity-manager |
| Identity Governance | Granular control of all identities and permissions across the entire organization, including risk scoring, access verification and recertification processes, and role mining. Can also be deployed without Identity Manager. | https://www.microfocus.com/en-us/cyberres/identity-access-management/identity-governance |
| Data Access Governance | Extends the same level of control to unstructured data such as documents, files, and email attachments. Policies can be used to automatically monitor and protect the policies efficiently. | https://www.microfocus.com/en-us/cyberres/identity-access-management/data-access-governance |
More details on IGA
Increasing digitization means more devices, users, and data in on-premises and multi-cloud/remote environments. The more complex the digitization, the more important becomes good management of identities and their access.
The problem is that complex IT ecosystems make it difficult and time-consuming to manage users and accesses effectively. This is where IGA can provide a solution. With an IGA solution, every access can be controlled and tracked for both on-premises and cloud-based systems.
How Identity Governance & Administration works
An IGA solution enables the entire lifecycle of user identities to be managed accurately and efficiently. In addition, administrators can automate both provisioning and deprovisioning of user access throughout the lifecycle. In the end, monitoring and reporting are also necessary to meet the compliance requirements.
Elements for Identity Administration (IA)
- Entitlement Management. Administrators define and verify what users are allowed to do in various applications and systems.
- Connectors. They connect the solution with the surrounding systems.
- Provisioning engine. It automatically takes user- and application-level access permissions from the vault and passes them to the peripheral systems via the connectors.
- Automated workflows. They manage access requests and approvals.
- Self-Service Portal. This is where users manage themselves. They apply for rights, reset passwords independently, or edit their master data.
Elements for Identity Governance (IG)
- Segregation of Duties (SoD). A set of policies that prevents risky or mutually exclusive rights from being assigned to a single person.
- Access Review. A process that analyzes, verifies, and, if necessary, revokes all of a user’s privileges. Also called recertification.
- Role-based Access Management (RBAC). Automated assignment of access rights based on role affiliations.
- Analyses and reports. They provide an overview of all user activities, indicate security problems, raise alarms, and ensure compliance.
Benefits of IGA
IGA can significantly improve the way an organization ensures its IT security.
– Simplified management of the entire identity life cycle
– Tracking of dangerous access requests
– Reporting for improved security and compliance
– Minimization of costs and errors through automation
– Higher security by minimizing the attack vector
– Minimization of unintentional mishaps through the least privilege principle
– Improvement of productivity through flexible access
– Support of enterprise scalability.
The difference between IGA and IAM
IGA is a subcategory of IAM. However, IGA systems provide additional functionality beyond standard IAM’s and help address common IAM issues. One of these is inappropriate and/or outdated access to corporate resources, which is minimized through access reviews. Others include remote workforce issues, time-consuming provisioning processes, weak Bring Your Own Device (BYOD) policies and strict compliance requirements. These problem points increase security risk and weaken enterprises’ compliance posture. With the help of IGA, enterprises can strengthen their IAM systems and overcome these challenges.
In addition, IGA enables automating access approval workflows and reduces risks. Policies can be defined and most importantly, enforced. For this reason, many organizations are using IGA to meet the compliance requirements of GDPR, BAFIN, FINMA, KRITIS, HIPAA, SOX, PCI DSS, etc. In today’s complex IT and cybersecurity landscape, IGA solutions are a critical foundation for organizations to protect themselves, improve resilience, serve customers, and achieve growth.
