Latest
Insights. Expetise
On the market since 1987.
Having implemented and operated Identity & Access Management solutions since the turn of the millennium, we hold extensive experience and expertise that we are glad to share with you. One man, no man – join our experts in continuous adventure of exploring IAM/IDM.
Key Stats
Acting now can save you millions.
%
of all data breaches involve credentials

a cyberattack is projected to occur every 39 seconds.
* according to University of Maryland
$23 trillion
the annual average cost of cybercrime predicted to be hit in 2027 for cyber and emerging technologies
* according to data cited by Anne Neuberger, U.S. Deputy National Security Advisor
PRODUCT UPDATES
Be the first to learn about new features of our products
Here you find the information regarding the latest SKyPRO products’ updates.
Jan 11, 2023 | 6 min read
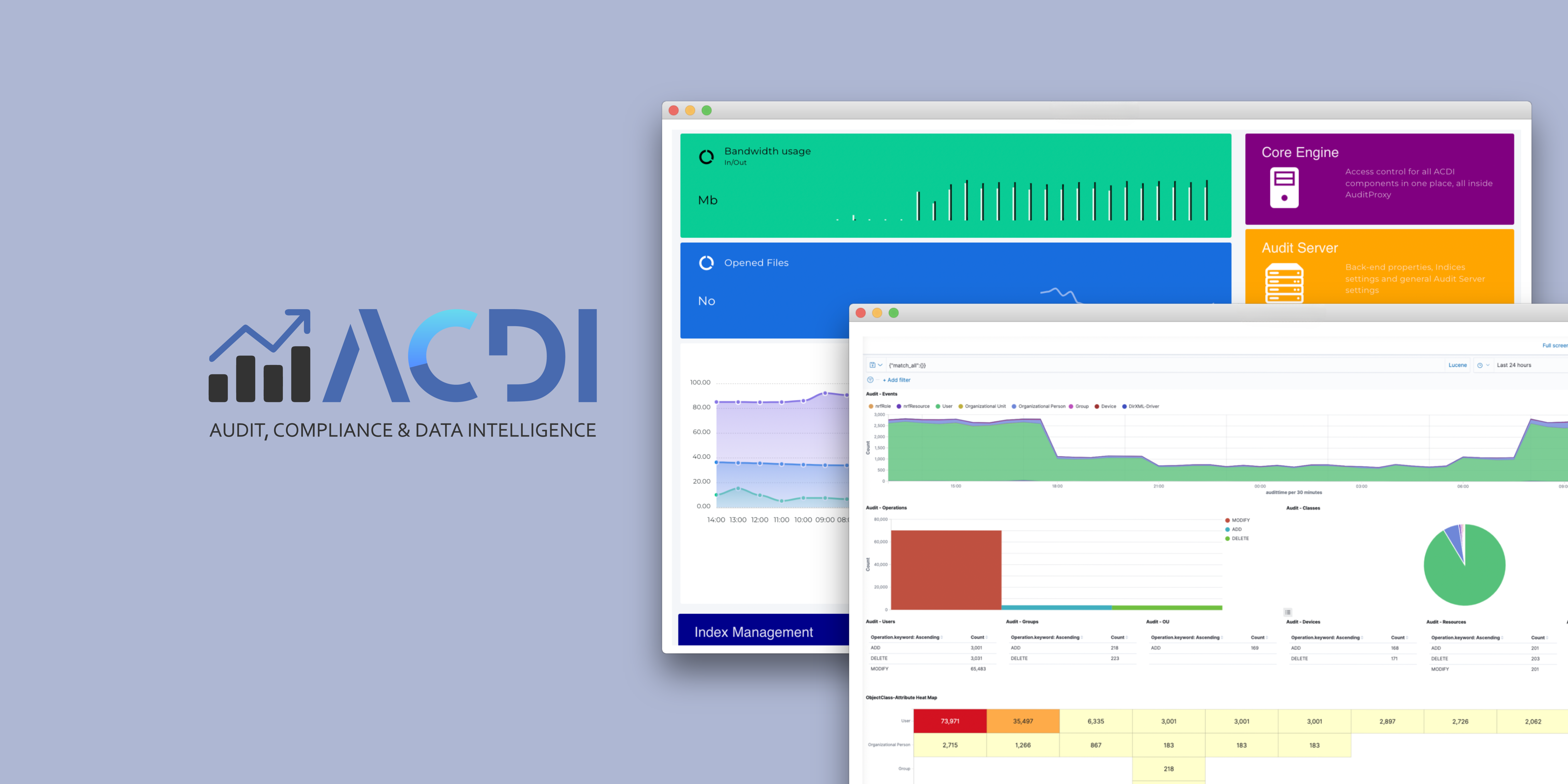
Welcome Audit, Compliance & Data Intelligence (ACDI) v4
Building something helpful is hard. You must know your customers – their challenges and needs. You have to do a lot of analysis, take risks, and get people to believe that your product is worth trying. But how can you find out if people are...

Florian Meile
Identity & Access Management expert. Rock-solid cybersecurity advisor. SKyPRO Executive Board member.
EXPERT INSIGHTS
Gain a unique, deep insight into the IAM/IDM branch
For decades we’ve been serving organizations around the world by developing, implementing and consulting around Identity & Access Management. Now, our experts share their professional experiences and obtained knowledge on various IT & IAM topics with you.

EXPERTS INSIGHTS
Monitoring of IDM system: why do you need it for cybersecurity?
Don’t let anything challenge your organization’s cybersecurity.

EXPERTS INSIGHTS
Cyber resilience through Identity Management
Cyber attacks are not a horrifying story for your company. Here’s how you increase the defense against them.
EXPERTS INSIGHTS
AI: The best (or worst) friend of Identity Management?
Find out from our experts how AI impacts Identity Management, if it can redefine IDM, and what to expect from it in the future.
AI: The best (or worst) friend of Identity Management?
Find out from our experts how AI impacts Identity Management, if it...
Overcoming Identity & Access Management (IAM) integration challenges
Integration challenges? Identity crisis? We didn’t hear about it....
4 Common Blunders Companies Make When Automating Identity Management Processes
Your guide to unforgivable mistakes that turn the Identity...
BASIC KNOWLEDGE
Get familiar with Zero Trust
The security model you should (not?) implement now.

BASIC KNOWLEDGE
Digital Identity & digital transformation
How Identity and Access Management gets the digital transformation off the ground.
BASICS
MUST-know for every IT/IAM/IDM specialist
For decades we’ve been serving organizations around the world by developing, implementing and consulting around Identity & Access Management. Now, our experts share their professional experiences and obtained knowledge on various IT & IAM topics with you.
![]()
BASIC KNOWLEDGE
Strengthening trust through Identity Management
Learn how your organization can combine Identity Management and digital trust