Governance Risk Compliance
The 3 most important levels of action
Manual data management is very time-consuming, costly, and also prone to errors.
Companies have to invest more and more effort to meet government requirements.
Processes and measures are becoming increasingly stressful.
For this reason, a secure IAG solution is the core of information security!
By automating the identity life cycle and integrating it into complex IT landscapes, security is increased and costs are reduced.
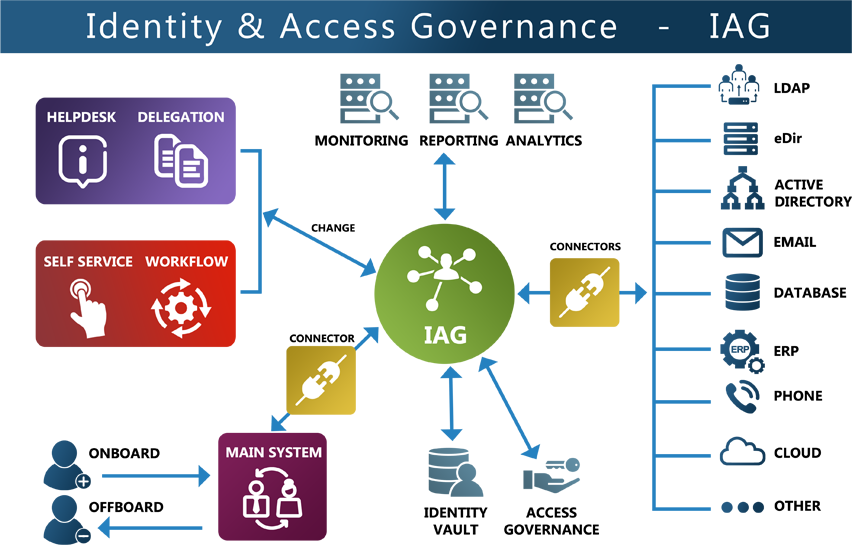
SKyPRO guarantees an Identity & Access Governance solution, which ...
- manages the Identity Life Cycle using automated processes
- reduces the risk of security breaches
- shortens response times
- increases transparency
- simplifies tasks
- reduces costs and resources
Governance
Ensuring & supporting the strategies and goals.
Risk Management
Carry out regular risk analysis. Strategies for minimizing risk and preparing loss buffers.
Compliance
Implementation, control, and compliance of the processes.
The foundation of the IAG solution
The Identity Life Cycle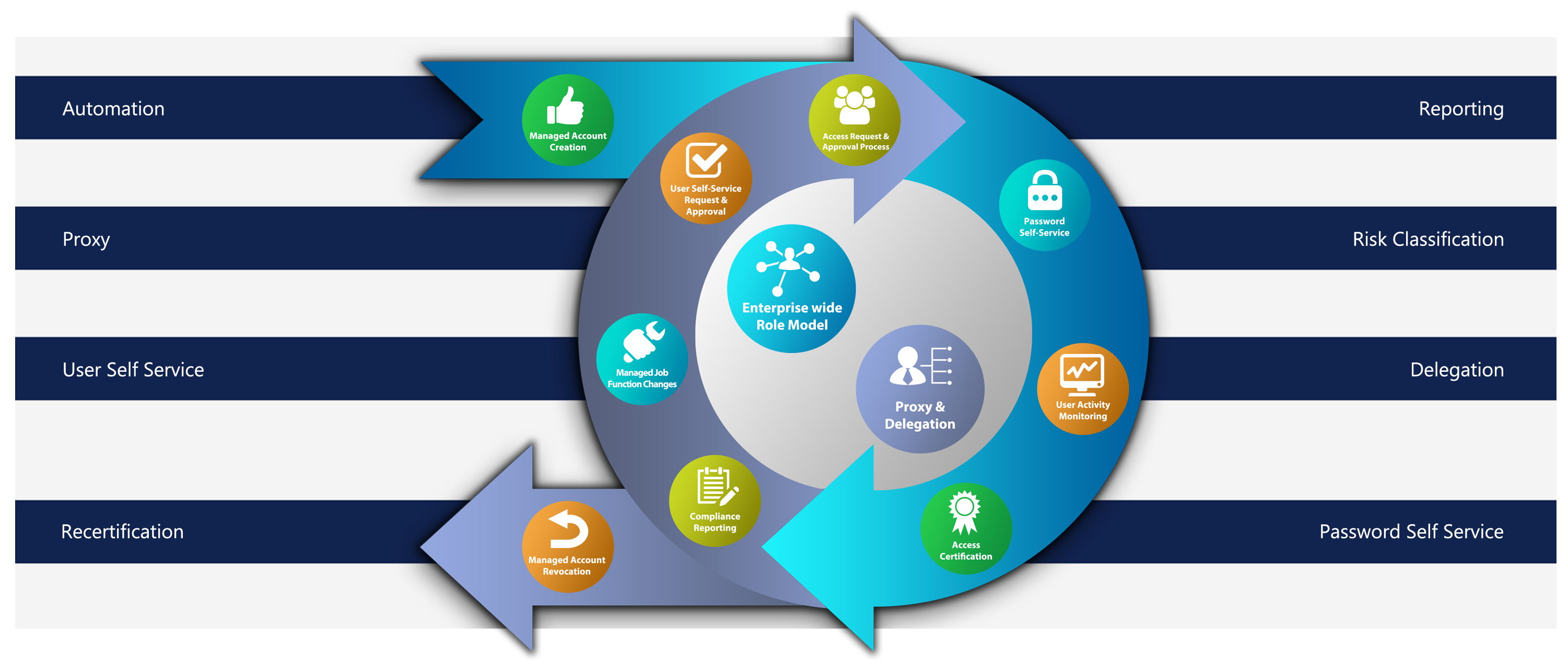
3 Functional Pillars of a good IAG Solution:
1. Identity Management
- Fully automatic provision of identities
- Integration of cloud solutions & external users
- As many self-service systems as possible should be implemented
2. Access governance
- Cost savings
- Cleansing creates the prerequisite for proper role management
- Support of risk management
3. Compliance Monitoring, Analytics & Reporting
- Regular risk analyzes
- Form the basis for authorizations
- Permanent monitoring through regular analyzes and controls
Facts
- Data security is a fundamental requirement of a modern company.
- Billions are spent on security systems every year.
- In 2018 there were 6,515 data breaches and over 5 billion data records stolen.
- Security inevitably leads to digital identity and its management.

What to do now:
1. Process & workflow automation
- Ensure that all processes are effectively automated
- Use permissions
2. Role-based rights management (RBAC)
- Create a role model
- Group & classify all data within the company
- Classification according to hazard potential
- Assignment of the responsible person
3. Continuous monitoring (reporting & auditing)
- Carry out regular reports and audits
- Every access must be monitored
A good governance solution recognizes and presents the current status of your system at all times!

Brochure
If you are interested in GRC and would like to find out more, we recommend that you take a look at our brochure!
